📝 MY NOTES #14 - The dynamic duo of data and ML engineering in cybersecurity
Theme - Cybersecurity 101 + Role of Analytics
Hello everyone,
Few weeks ago I had the chance to attend the Data Summit 2024 where speakers from different organizations spoke about a myriad of topics related to data. There were 10 sessions given by people who were CEOs, Data Managers, Data Engineers. Below are the titles of all the sessions I attended. In the coming weeks I will be posting my notes from each of these sessions & these titles will turn into links that you can use to jump between different session notes -
Beyond the Basics: The last 10 things data teams think about
Building a shared foundation of trust through data storytelling
The dynamic duo of data and machine learning engineering in cybersecurity
Your Company's Success isn't Measured in megabytes, it's measured in impact!
Let’s start with the 8th session I attended-
The dynamic duo of data and machine learning engineering in cybersecurity
The Speaker :
John Benito JP, Senior Manager, Data Science & Engineering at Capital One
John starts by mentioning that in today's world data is stored everywhere whether its texts in our phones, pictures we take, our fitness tracker etc etc. Each & every activity we perform on our devices are being logged, extracted, transformed somewhere whether local or cloud. All these information are very sensitive information which need to be safeguarded from certain parties who are interested in this data for malicious use, Cybersecurity comes to play to make sure all of this data, devices are secure.
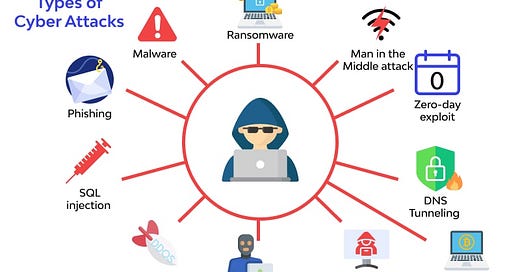
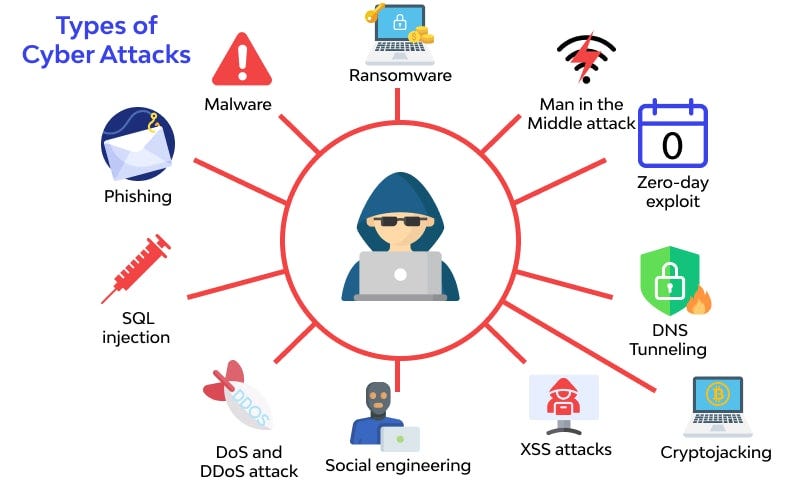
The malicious cyberattack activities could be carried out in different ways in order to achieve this critical data -
Phishing: Phishing attacks involve the use of fraudulent emails, messages, or websites to deceive individuals into divulging sensitive information such as passwords, credit card numbers, or personal data. These attacks often mimic legitimate sources, exploiting trust to trick recipients into taking actions that benefit the attacker.
Malware: Malware, short for malicious software, refers to any software designed to harm, disrupt, or gain unauthorized access to a computer system. This includes viruses, worms, trojans, spyware, and ransomware. Malware can infect systems through various means, such as malicious email attachments, compromised websites, or infected USB drives.
Ransomware: Ransomware is a type of malware that encrypts a victim's files or entire system, rendering them inaccessible until a ransom is paid. Ransomware attacks typically demand payment in cryptocurrency and can have severe consequences, including financial loss, data breach, and operational downtime.
Man-in-the-Middle (MitM) Attack: In a MitM attack, an attacker intercepts communication between two parties without their knowledge, allowing them to eavesdrop on or manipulate the exchange of information. This can occur in various scenarios, such as unsecured Wi-Fi networks, compromised routers, or malicious software.
Zero-day Exploit: A zero-day exploit targets vulnerabilities in software or hardware that are unknown to the vendor or the public. Attackers exploit these vulnerabilities before a patch or fix is available, making them particularly dangerous as there is no defense against them until they are discovered and mitigated.
DNS Tunneling: DNS tunneling is a technique used to bypass firewalls and exfiltrate data from a network by encoding it within DNS queries and responses. Attackers exploit vulnerabilities in DNS servers or use specially crafted malware to establish covert communication channels, allowing them to transfer sensitive information undetected.
Cryptojacking: Cryptojacking involves the unauthorized use of a victim's computing resources to mine cryptocurrency. Attackers inject malicious scripts or malware onto devices, exploiting their processing power to mine cryptocurrency for the attacker's benefit. This can lead to increased energy consumption, system slowdowns, and potential damage to hardware.
Cross-Site Scripting (XSS) Attacks: XSS attacks occur when attackers inject malicious scripts into web pages viewed by other users. These scripts can execute arbitrary code in the victim's browser, leading to various security vulnerabilities such as data theft, session hijacking, or defacement of web pages.
Social Engineering: Social engineering attacks manipulate individuals into divulging confidential information or performing actions that compromise security. This can include pretexting, phishing, baiting, or impersonation to exploit human psychology and trust relationships for malicious purposes.
Denial-of-Service (DoS) & Distributed Denial-of-Service (DDoS) Attacks: DoS and DDoS attacks aim to disrupt or disable the availability of a targeted system or network by overwhelming it with a flood of traffic or requests. These attacks can render services inaccessible, causing financial losses, reputation damage, and operational disruptions.
SQL Injection: SQL injection attacks exploit vulnerabilities in web applications that use SQL databases by inserting malicious SQL code into input fields. This allows attackers to manipulate database queries, access unauthorized data, modify or delete records, and execute arbitrary commands on the underlying database server.
How is Cybersecurity achieved?
Cybersecurity is achieved through a multi-faceted approach that encompasses various measures, including technical controls, administrative controls, and awareness and training programs. Each of these components plays a crucial role in protecting against cyber threats and ensuring the security of computer systems, networks, and data. Let's explore how each of these means contributes to cybersecurity:
Technical Controls:
Technical controls involve the implementation of security measures within the IT infrastructure to prevent unauthorized access, detect and respond to security incidents, and protect against cyber threats. These controls include:
Access controls: Implementing user authentication mechanisms, such as passwords, biometrics, or multi-factor authentication, to verify the identity of users and limit access to authorized individuals.
Encryption: Encrypting sensitive data both in transit and at rest to protect it from unauthorized access or interception by hackers.
Firewalls and intrusion detection/prevention systems (IDS/IPS): Deploying firewalls and IDS/IPS solutions to monitor network traffic, detect suspicious activities, and block malicious traffic.
Endpoint security: Installing antivirus software, anti-malware programs, and endpoint detection and response (EDR) solutions to protect endpoints, such as computers, laptops, and mobile devices, from malware and other cyber threats.
Patch management: Regularly applying software patches and updates to address security vulnerabilities and ensure that systems are up-to-date with the latest security fixes.
Administrative Controls:
Administrative controls involve the implementation of policies, procedures, and guidelines to manage security risks, establish accountability, and ensure compliance with regulatory requirements. These controls include:
Security policies and procedures: Developing and enforcing security policies and procedures that define acceptable use of IT resources, data handling practices, incident response procedures, and other security-related guidelines.
Risk management: Conducting risk assessments, identifying security threats and vulnerabilities, and implementing risk mitigation strategies to reduce the likelihood and impact of security incidents.
Incident response planning: Establishing incident response teams, procedures, and communication channels to effectively respond to security incidents, minimize damage, and restore normal operations.
User access management: Managing user accounts, permissions, and privileges to ensure that users have appropriate access levels based on their roles and responsibilities.
Security awareness training: Providing training and education programs to employees, contractors, and other stakeholders to raise awareness of cybersecurity threats, best practices, and compliance requirements.
Awareness and Training:
Awareness and training programs are essential for educating employees and stakeholders about cybersecurity risks and promoting a culture of security awareness within the organization. These programs include:
Security awareness training: Offering regular cybersecurity awareness training sessions, workshops, and online courses to educate employees about common cyber threats, social engineering tactics, phishing scams, and best practices for protecting sensitive information.
Phishing simulations: Conducting simulated phishing attacks to test employees' awareness and response to phishing emails, and providing feedback and training to improve their ability to recognize and report suspicious emails.
Security awareness campaigns: Launching awareness campaigns, newsletters, posters, and other communication initiatives to reinforce security messages, promote good security habits, and encourage reporting of security incidents.
What are the challenges faced in Cybersecurity ?
Cybersecurity faces an array of challenges in today's digital landscape, each presenting its own set of complexities and risks. Here's an overview of some prominent challenges along with their subtopics:
Evolving Sophisticated Attackers:
Advanced Persistent Threats (APTs): Sophisticated attackers, often state-sponsored or well-funded, employ APTs to infiltrate systems and remain undetected for extended periods.
Zero-day Exploits: Attackers leverage vulnerabilities unknown to the vendor or public, making them difficult to defend against until patches are developed. Remote work environments may introduce additional challenges in applying patches promptly across a dispersed workforce, leaving systems vulnerable to zero-day exploits.
Social Engineering: Attackers exploit human psychology to manipulate individuals into divulging sensitive information or performing actions that compromise security.
Expanding Attack Surface:
IoT Devices: The proliferation of Internet of Things (IoT) devices increases the attack surface, as each device represents a potential entry point for cyber threats.
Cloud Services: The adoption of cloud computing introduces new security challenges, including data breaches, misconfigurations, and unauthorized access to cloud resources.
BYOD (Bring Your Own Device): With the rise of remote work and mobile devices, organizations struggle to secure personal devices used for work, leading to increased vulnerability.
Insider Threat:
Malicious Insiders: Employees or contractors with authorized access exploit their privileges to steal sensitive data, sabotage systems, or disrupt operations.
Negligent Insiders: Unintentional actions by employees, such as clicking on malicious links or misconfiguring security settings, can inadvertently expose organizations to cyber threats.
Third-party Vendors: Businesses often rely on third-party vendors for various services, but these vendors can pose insider threats if they are compromised or engage in malicious activities.
Regulations:
Compliance Challenges: Organizations must navigate a complex landscape of regulatory requirements, such as GDPR, HIPAA, and PCI DSS, to ensure they are compliant with data protection and privacy laws.
Cross-border Data Transfer: Global businesses face challenges in complying with conflicting data protection regulations across different jurisdictions, particularly regarding cross-border data transfers.
Regulatory Lag: The rapid evolution of technology often outpaces the development of cybersecurity regulations, leaving gaps in legal frameworks that cybercriminals can exploit.
How Data Engineering & AI help in achieving Cybersecurity?
Data Engineering
1. Data Collection: Data engineering facilitates the collection of vast amounts of security-related data from various sources, including network logs, system events, user activities, and external threat intelligence feeds.
2. Real-time Data Processing: By leveraging technologies like stream processing and complex event processing, data engineering enables organizations to analyze security data in real-time, allowing for immediate detection and response to security incidents.
3. Data Transformation and Enrichment: Data engineering involves transforming raw security data into meaningful insights by enriching it with contextual information such as threat intelligence feeds, user behavior analytics, and historical trends.
4. Data Storage and Retrieval: Data engineering ensures efficient storage and retrieval of security data, enabling organizations to store large volumes of data cost-effectively while ensuring quick access for analysis and investigation purposes.
5. Scalability and Performance: Data engineering principles are applied to design scalable and high-performance cybersecurity systems capable of handling growing volumes of data and processing demands as the organization's needs evolve.
6. Observability: Data engineering practices promote observability in cybersecurity systems, allowing organizations to monitor the health, performance, and security of their infrastructure, applications, and data pipelines in real-time.
Artificial Intelligence
1. Threat Detection and Prediction: AI-powered algorithms analyze vast amounts of security data to detect known and unknown threats, identifying patterns and anomalies indicative of malicious activity. AI models can also predict emerging threats based on historical data and trending patterns.
2. Behavioral Analysis: AI-based behavioral analytics analyze user and entity behavior to detect deviations from normal patterns, such as unusual access patterns, unauthorized privilege escalation, or suspicious network traffic, indicating potential insider threats or compromised accounts.
3. Automated Response: AI enables automated response mechanisms to rapidly mitigate security incidents by triggering predefined actions or policies in response to detected threats. This includes automatically blocking malicious IP addresses, quarantining infected devices, or isolating compromised systems from the network.
4. Continuous Learning: AI algorithms continuously learn and adapt to evolving threats and changing environments by ingesting new data and feedback from security operations. This enables AI-powered cybersecurity systems to improve detection accuracy over time and stay ahead of emerging threats.
In conclusion, the synergy between data teams and cybersecurity teams forms a formidable united front in the face of cyber adversaries. By combining their expertise, resources, and insights, these teams can effectively anticipate, detect, and respond to cyber threats with agility and precision.
Together, they create a culture of collaboration, innovation, and resilience, strengthening the organization's ability to safeguard its assets, data, and reputation in an increasingly complex and dynamic threat landscape. As partners in cybersecurity defense, data teams and cybersecurity teams play a vital role in securing the digital ecosystem and ensuring the continuity and success of the organization in an ever-evolving digital age.
What has been your experience with Cybersecurity. Have you ever faced malware attack or hacking attempts? For me almost every other week at my job!
Until next edition,
Raghunandan 🎯
& If it’s your first time here, TheWeekendFreelancer currently has 5 ongoing series - Tools 🛠️, Maths 📈, Domain 🌐, Trends 📻 & My Notes 📝. Have fun reading!
P.S. - “The Weekend Freelancer” is a reader backed publication. Share this newsletter with your friends and relatives & consider becoming a free or paid member of this newsletter. Every subscription gives me an extra ounce of motivation to keep going 💪!
You can also support my work here. Cheers!